Sonne Finance Hack: When Forking Code Costs $20 Million
Everything about this exploit was avoidable. The vulnerability was known. The fix was simple. The warning signs were everywhere. Sonne Finance paid $20 million to learn a lesson that was already taught three times before.

On May 14, 2024, users of Sonne Finance learned that trust isn’t enough.
In 25 minutes, an attacker drained $20 million from the protocol using a vulnerability that wasn’t new, wasn’t sophisticated, and wasn’t even a secret. The same exploit had already hit three other protocols in the previous 12 months. Sonne Finance had been warned by their auditors. The fix was well-documented.
And yet, it happened anyway.
What makes this exploit particularly instructive isn’t the technical complexity, it’s the simplicity. This is a case study in what happens when teams fork code they don’t fully understand, ignore audit warnings, and deploy critical infrastructure without proper operational security.
Here’s exactly how it went down, why it keeps happening, and what it means for the future of DeFi security.
// TL;DR – The $20 Million Lesson
What happened:
- $20 million stolen from Sonne Finance on Optimism on May 14, 2024.
- Attack method: Precision loss “donation attack” exploiting empty Compound V2 market.
- Historical context: Same vulnerability had already hit Hundred Finance ($7.4M), Onyx Protocol. ($2M), and Starlay Finance ($2.1M)
- Audit warning: yAudit specifically flagged this exact vulnerability in their security report.
- Root cause: Permissionless timelock execution on Optimism + empty market initialization + ignored audit findings.
- Laundering: Funds immediately bridged to multiple chains via Stargate Finance.
Why it matters:
- Over 100 active Compound V2 forks exist.
- Demonstrates risk when teams fork code without understanding it.
- Shows that audits are meaningless if teams don’t actually fix the findings
- Proves that operational security (deployment procedures) is just as critical as code security.
Table of Contents ▼
// What is Sonne Finance?
Sonne Finance is a decentralized lending protocol on Optimism and Base. Users deposit crypto to earn interest, others borrow by providing collateral. Users deposit WETH and receive “soWETH” tokens representing your share of the pool. As interest accrues, each soWETH becomes worth more WETH.
The critical detail: Sonne Finance is a fork of Compound V2 i.e. they copied Compound’s open-source code and deployed it on Layer 2 networks.
Forking successful code is common in DeFi, but here’s the problem: Compound V2 has documented edge cases and deployment requirements that must be handled carefully. If you fork without understanding these nuances, you inherit the attack surface without the expertise to defend it.
As of May 14, 2024, Sonne Finance had significant TVL across both chains. Within 25 minutes, $20 million was stolen through a vulnerability that had already been exploited three times before.
// The Vulnerability: Compound V2’s Empty Market Problem
When you deposit 100 USDC into Sonne Finance, you receive soUSDC tokens representing your share of the pool. This is tracked through an exchange rate:
exchangeRate = (totalCash + totalBorrows – totalReserves) / totalSupply
Simple example: Pool has 1M USDC, 500K borrowed, 50K in reserves, and 1M soUSDC tokens. Exchange rate = 1.45 USDC per soUSDC.
The stock share analogy: If a company has $100M in assets and 100M shares, each share is worth $1.00. But what if it had only 2 shares? Each would be worth $50M. If you could manipulate the asset balance while keeping shares constant, you could make those 2 shares worth whatever you want.
That’s the core vulnerability.
The Empty Market Problem
When a new market deploys, totalSupply starts at zero. Even after the first deposit, if it’s microscopic (say, 2 wei), totalSupply remains tiny. Solidity uses integer division, which rounds down. When you combine minuscule totalSupply with large donations, rounding errors become exploitable.
The “Donation Attack” Pattern
- Find newly deployed market (totalSupply = 0 or tiny)
- Mint minimal tokens (deposit 0.0000004 VELO → get 2 wei soVELO)
- “Donate” massive amount (direct transfer 35M VELO to contract)
- Exchange rate explodes (2 wei soVELO now “worth” 35M VELO)
- Exploit precision loss (redeem 35M VELO for only 1 wei soVELO due to rounding)
- Repeat on other markets, profit $20M
The donation increases totalCash without changing totalSupply, inflating the exchange rate. Then Solidity’s rounding allows redeeming massive amounts for tiny token burns.
This vulnerability was first documented after Hundred Finance’s April 2023 exploit. By May 2024, it had worked successfully three times. The attack pattern was well-known, documented, and preventable.
// Timeline: How the Attack Unfolded
May 4, 2024: The Setup
Sonne Finance’s governance approved SIP-015: Add VELO markets to Optimism. The proposal passed. The team prepared deployment.
May 12, 2024: The Vulnerability Window Opens
The team scheduled deployment on their multisig with a 2-day timelock. Standard security practice so queued transactions give the community time to review.
Critical detail: On Optimism, timelock execution was permissionless. After the delay, anyone could execute. On Base, only authorized addresses could execute. This difference proved devastating.
May 14, 2024 – 22:18:15 UTC: The Attack
The timelock expired. The attacker won the race.
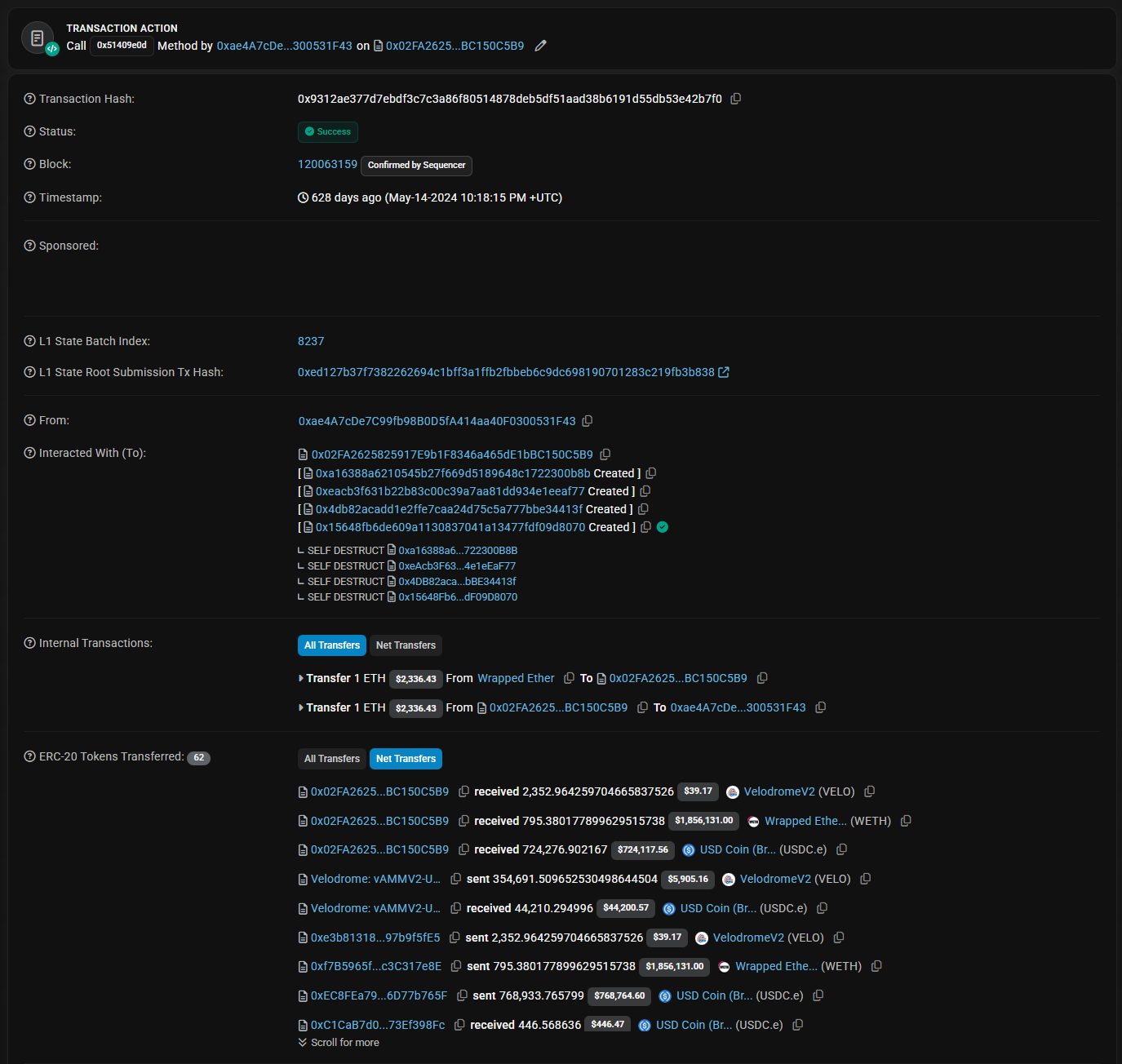
The exploit transaction on Optimistic Etherscan, May 14, 2024, 10:18:15 PM UTC (628 days ago). Shows 2,352 VELO, 795 WETH, and 724,276 USDC received by attacker’s contract. Status: Success.”
In one transaction, the attacker:
- Executed the “create VELO market” proposal.
- Added their own collateral factor (35% instead of planned 0%).
- Immediately began the donation attack.
Because Optimism lacks sophisticated MEV infrastructure, the attacker just needed to submit first. No bribes, no auctions, just timing.
Attack execution (~5 minutes):
- soVELO market: Mint 2 wei tokens, flash loan 35M VELO, donate, redeem → ~$7.8M
- soUSDC market: Repeat → ~$4.5M
- soWETH market: Repeat → ~$7.7M
- Total stolen: ~$20M in under 5 minutes
Small victory: ~$6.5M was saved when Seal contributors rushed to add $100 of VELO to one market, increasing totalSupply enough to make the attack impractical. This proves the attack was time-sensitive but also that the team shouldn’t have created this race condition.
22:43 UTC (+25 minutes): Team Response
Sonne Finance’s official post-mortem, May 14, 2024. Team acknowledged ‘known donation attack to Compound v2 forks’ and that multisig execution was ‘permissionless on Optimism’ but not on Base. The key difference.
The team noticed 25 minutes later. They immediately paused Optimism markets and confirmed Base was safe. Published post-mortem, offered 10% bounty ($2M), but the funds were never returned.

// Why This Happened: The Triple Failure
Failure #1: Known Vulnerability Ignored
The same vulnerability had already been exploited three times:
- Hundred Finance (April 2023): $7.4M
- Onyx Protocol (November 2023): ~$2M
- Starlay Finance (February 2024): ~$2.1M
Each used identical donation mechanics. Security firms published post-mortems. The pattern had a name: “empty market donation attack.”
Sonne Finance had 13 months to learn from Hundred’s mistake. Multiple blogs explained it. Audit firms checked for it. Twitter threads warned about it.
And yet, it worked again. For $20 million.
As security researchers noted: It’s tragic that protocols keep learning the hard way that you shouldn’t fork code you don’t understand.
Failure #2: Audit Warning Explicitly Ignored
Sonne Finance knew about this risk. They were audited by yAudit (Yearn Finance’s security team), which flagged a HIGH severity finding explicitly about this vulnerability.
According to their post-mortem and security analyses, the audit warned that the protocol “does not appear to have any mitigations in place to prevent this attack when a new market is deployed,” specifically referencing the Hundred Finance exploit.
What the team did:
- Acknowledged the finding
- Designed “multi-step deployment” as mitigation
- Implemented timelocked transactions
What went wrong:
- Multi-step process created a race condition
- Relied on executing first after timelock
- Didn’t account for permissionless execution
From their own post-mortem:
“We avoided the issue in the past, by adding the markets with 0% collateral factors, adding collateral and burn them, only then increase the c-factors.”
They knew the correct procedure. They’d done it before. But splitting it into multiple transactions created the vulnerability window that cost $20 million.
The lesson: Audit findings aren’t suggestions. Complex workarounds fail under adversarial conditions. Simple, atomic fixes work.
Failure #3: Optimism vs Base Configuration
Only Optimism got exploited. Base was completely safe. Same code, different configuration, $20M difference.
From their post-mortem:
“Our multisig execution is not permissionless Base, but permissionless on Optimism.”
On Optimism, anyone could execute queued transactions after the timelock. The attacker monitored the timelock, knew exactly when execution became possible, and front-ran the team.
The team queued TWO transactions:
- Create VELO market
- Set collateral factor to 0% (safety)
Fatal flaw: Should have been ONE atomic transaction. By splitting them, they created a window where the market existed but wasn’t protected. The attacker executed transaction 1 with their own collateral factor setting and immediately exploited the empty market.
// Following the Money: Cross-Chain Laundering
Through blockchain forensics, I tracked the stolen funds through the laundering process, revealing how attackers use legitimate DeFi infrastructure to make recovery impossible.
The Distribution
Initial attacker wallet (0xae4a…1f43) showing complete transaction history. Exploit occurred 628 days ago (May 14, 2024), with funds quickly moved out.
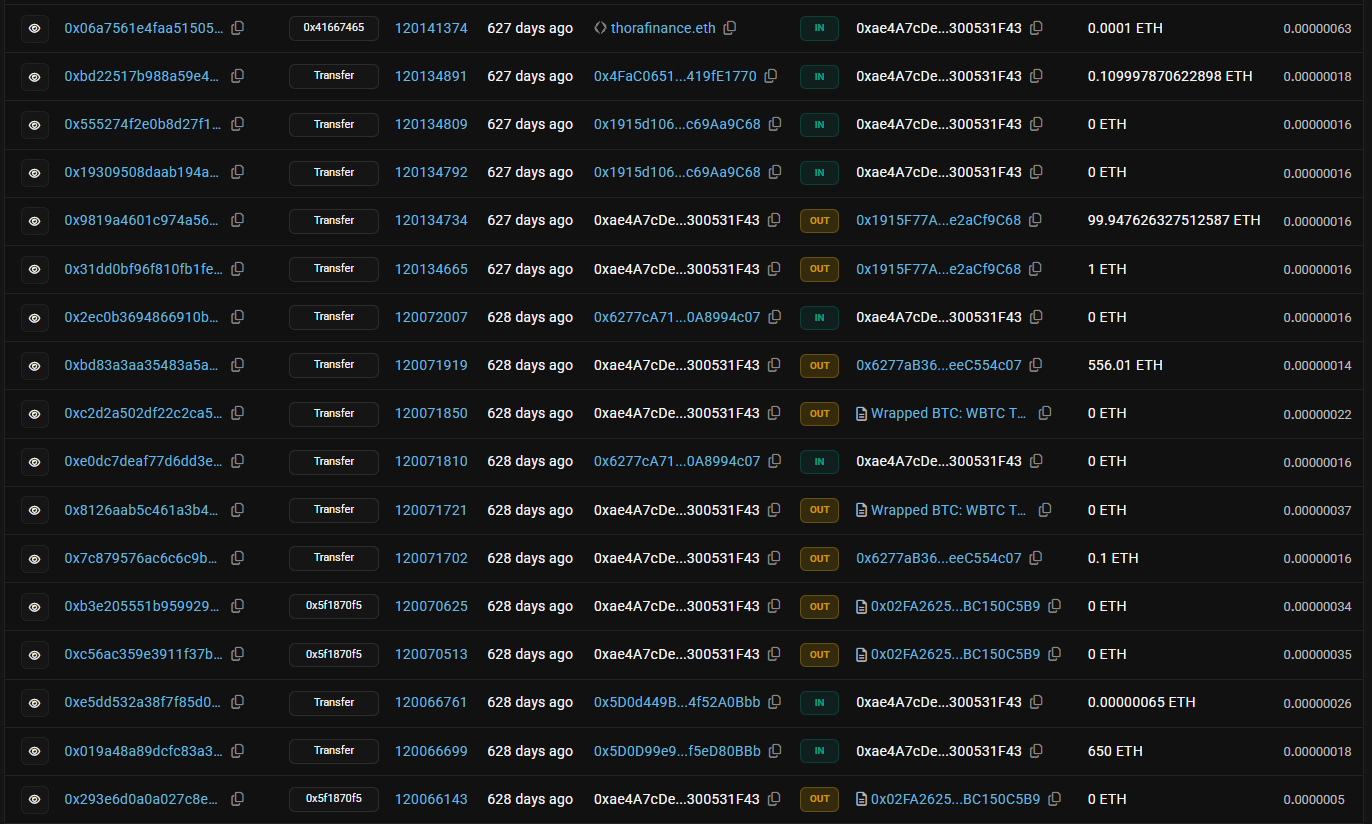
According to the official post-mortem, funds were split across multiple addresses:
- 0x5d0d99e9886581ff8fcb01f35804317f5ed80bbb: ~$10.67M
- 0x6277ab36a67cfb5535b02ee95c835a5eec554c07: ~$7.79M
- 0xae4a7cde7c99fb98b0d5fa414aa40f0300531f43: ~$293K
- 0x9f09ec563222fe52712dc413d0b7b66cb5c7c795: ~$95K
This serves two purposes: risk distribution (if one wallet freezes, others survive) and transaction size reduction (smaller amounts avoid alerts).
The Cross-Chain Bridge
By tracking attacker wallets through multiple hops, stolen funds were systematically moved through Stargate Finance’s ETH Router.
Multiple transactions of 31-39 ETH each, 624 days ago (May 2024), show systematic bridging of stolen funds to other chains.
What is Stargate Finance? A cross-chain bridge built on LayerZero (the same infrastructure I’ve analyzed in previous articles). It enables moving assets between Optimism, Ethereum, Arbitrum, BSC, Polygon, and more.
The protocol is completely legitimate. Millions use it daily. It’s crucial DeFi infrastructure. But it’s also perfect for money laundering.
The Multi-Chain Strategy
The attacker didn’t send everything to one destination. Blockchain analysis reveals they split laundering across multiple chains:
- Some funds → Ethereum mainnet (access to Tornado Cash)
- Some funds → Arbitrum (different ecosystem)
- Likely other chains (BSC, Polygon, etc.)
Why multiple chains?
What starts as one investigation on Optimism becomes:
- Investigation #1: Optimism (the theft)
- Investigation #2: Ethereum (track bridged funds)
- Investigation #3: Arbitrum (track other bridged funds)
Each chain has different explorers, privacy tools, exchanges, and jurisdictions. Tracking requires 3-5x the resources, and by the time you map one path, funds on other chains are already laundered.
The Complete Flow
The Irony
In previous articles, I praised LayerZero and Stargate for enabling seamless cross-chain transfers, capital efficiency, and blockchain interoperability. All of that remains true.
But tracking this laundering forced me to confront reality: The technology that makes DeFi powerful makes crypto crime nearly unstoppable.
For legitimate users: “I can move USDC from Optimism to Arbitrum in minutes!” – TRUE.
For attackers: “I can launder stolen funds across chains in minutes!” – ALSO TRUE.
The protocol can’t distinguish. That’s the point of permissionless finance.
The uncomfortable truth: You can’t have permissionless, censorship-resistant finance AND the ability to stop bad actors. You have to choose. DeFi chose permissionless.
Could Stargate Have Stopped This?
No, and they shouldn’t be expected to. Stargate is a protocol. Smart contracts executing mathematical rules, not human judgment. They cannot freeze funds, block addresses, or know which funds are stolen.
If bridges could freeze funds arbitrarily, they’d be centralized points of failure, subject to government pressure, vulnerable to corruption, not really “decentralized.”
Prevention must happen earlier:
- Level 1: Don’t get exploited (Sonne failed)
- Level 2: Immediate response (partial—25 min too late)
- Level 3: Exchange intervention (unknown status)
Current Status
After bridging through Stargate, funds likely underwent further laundering: privacy mixers, atomic splits, time-based aging, multiple chains, gradual exchange cashouts.
Nearly two years later (February 2026), none of the $20 million has been publicly recovered.
One attacker wallet showed minor activity in January 2026 (a small gas refund transaction). But all significant funds left within days of the original exploit. The attacker successfully used multiple layers (wallets, bridges, mixers, time) to make recovery exponentially harder.
The lesson: There is no “freeze account” in DeFi. Once funds leave the exploited protocol, they enter an ecosystem designed to resist control. The only defense is prevention.
// How It Could Have Been Prevented
Every aspect was preventable. Here are six specific fixes:
1. Initial Mint & Burn Pattern
Deploy markets with 1000+ tokens minted and burned to address(0). This ensures totalSupply can never be microscopically small, making the donation attack economically impractical. Aave, Uniswap V2, and others use this pattern. It’s a solved problem.
2. Atomic Market Deployment
Combine market creation and configuration in ONE transaction. Sonne split it into two (create market, then set c-factor), creating a race condition. Single transaction = no window for attack.
3. Permissioned Timelock Execution
Restrict execution to authorized addresses. Base was safe solely because only the team could execute. Optimism allowed anyone and the attacker won the race.
4. Collateral Factor 0% Initially
Even if deployment is imperfect, prevent borrowing until the market is proven safe. Limits blast radius. This was Sonne’s plan, they just didn’t execute it atomically.
5. Real-Time Monitoring
Monitor for exchange rate anomalies (sudden 10x+ jumps), large direct transfers to contracts, flash loan activity, and unusual redemptions. Tools like Forta, Tenderly, and OpenZeppelin Defender enable this. The $6.5M saved by community members proves fast response works. Automated systems would be even better.
6. Actually Fix Audit Findings
When auditors flag HIGH severity findings referencing $7M+ exploits that already happened, that’s a showstopper. Fix the root cause simply and atomically. Re-audit. Test adversarially. Then deploy.
// What This Means for DeFi
The Forking Problem
Over 100 active Compound V2 forks exist as of early 2026. Each is a potential target.
The false security: Teams assume “Compound is battle-tested, so we’re safe.”
The reality: Compound V2’s original deployment was managed by a team that deeply understood the code, knew edge cases, had operational security, and monitored constantly. When you fork without that knowledge, you inherit attack surface without expertise.
The scoreboard:
- Hundred Finance: $7.4M (April 2023)
- Onyx: ~$2M (November 2023)
- Starlay: ~$2.1M (February 2024)
- Sonne: $20M (May 2024)
- Total: ~$31.5M from ONE vulnerability
Four protocols exploited. Same attack. Over 18 months. And 100+ forks remain in production.
The Audit Theater Problem
Sonne got audited. Received HIGH severity finding. Acknowledged it. Implemented “mitigation.” Still got exploited for $20M.
The lesson: Audits find problems. Teams must solve them properly. Complex workarounds fail. Simple, fundamental fixes work.
The Systemic Question
How many of those 100+ forks properly protect against this attack? Will they learn from Sonne’s $20M lesson before becoming the fifth victim?
// Lessons
For Developers
- Don’t fork what you don’t understand. Read every line. Study historical exploits. Understand initialization requirements. If you can’t explain the exchange rate vulnerability, you’re not ready to deploy a Compound fork.
- Treat audit findings as absolute requirements. HIGH/CRITICAL severity = launch blocker. Fix the root cause simply, re-audit, test adversarially. Complex mitigations are signs you haven’t actually fixed it.
- Test deployment procedures adversarially. Have a red team try to exploit your deployment on testnet. If it relies on “being first to execute,” it’s broken. Ensure atomic operations with no race conditions.
- Implement monitoring before launch. Alert on exchange rate anomalies, donations, flash loans, unusual redemptions. The $6.5M saved proves fast response works.
- Learn from others proactively. When a fork gets exploited, immediately check if you’re vulnerable. Implement fixes before you’re the next victim.
For Users
- Research before depositing. Is it a fork? Of what? Has that code been exploited? Are there audits? Were findings fixed or just “mitigated”? How long has it been live?
- Diversify risk. Don’t put everything in one protocol, especially new forks (<6 months), protocols without comprehensive audits, or teams without proven incident response.
- Watch for high-risk periods. New market deployments, governance proposals touching critical contracts, and rushed upgrades are especially dangerous times.
- Accept DeFi reality. Smart contract risk is real and permanent. No insurance, no customer service, no undo button. Only deposit what you can afford to lose completely.
// Conclusion: The $20 Million Lesson
The Sonne Finance exploit wasn’t sophisticated. The attacker didn’t discover a novel vulnerability. They just executed a well-documented attack that had worked three times before.
What makes this tragic:
- Vulnerability known for 13 months
- Auditors warned explicitly (HIGH severity)
- Fix was simple (3 lines: mint, burn, configure)
- Three previous examples to learn from
- 100% preventable
What makes this important:
- Not about one protocol losing $20M
- About an ecosystem of 100+ vulnerable forks
- Millions in user funds potentially at risk
- Attackers have a proven playbook
Through blockchain forensics, the complete story:
Not just how the attack worked, but where the money went. Through Stargate to Ethereum and Arbitrum. Across chains, through mixers, into the laundering pipeline that makes recovery virtually impossible.
The same cross-chain infrastructure that enables DeFi’s promise — LayerZero, Stargate, interoperability — enabled the attacker to escape with $20 million. That’s not a bug, it’s the fundamental trade-off: Permissionless systems serve everyone equally.
For developers running Compound V2 forks:
Do you mint and burn initial tokens? Have permissioned execution? Set collateral factors to 0% initially? Deploy atomically? Have monitoring?
If any answer is “no,” you’re vulnerable. Fix it before becoming the fifth victim.
For users with funds in Compound V2 forks:
Check for proper security patterns. Maybe diversify to protocols with better track records.
The only defense is prevention. Perfect security before deployment. Because after the theft, the funds are gone.
In traditional finance, you call your bank and reverse transactions. In DeFi, code is law. When code is wrong, there’s no customer service, no insurance, no undo button. The blockchain executed exactly what it was told. The funds are permanently gone, laundered through legitimate infrastructure that can’t and won’t stop them.
- Sonne Finance learned this for $20 million.
- Hundred Finance for $7.4 million.
- Onyx for $2 million.
- Starlay for $2.1 million.
Will the other 100+ forks learn from their mistakes, or will they pay their own tuition?
The vulnerability is known. The fix is documented. The choice is yours.
Don’t be the fifth victim.
Alex Grant
Blockchain Infrastructure & Security Analyst
Hi, I’m Alex, founder of Web3Fuel, where I analyze cross-chain protocols and smart contract security through hands-on testing and blockchain forensics.
My goal is to simplify blockchain and provide fuel for the growth of Web3.
